|
Game Theory In Communication Networks
Game theory has been used as a tool for modeling and studying interactions between cognitive radios envisioned to operate in future communications systems. Such terminals will have the capability to adapt to the context they operate in, through possibly power and rate control as well as channel selection. Software agents embedded in these terminals will potentially be selfish, meaning they will only try to maximize the throughput/connectivity of the terminal they function for, as opposed to maximizing the welfare (total capacity) of the system they operate in. Thus, the potential interactions among them can be modeled through non-cooperative games. The researchers in this field often strive to determine the stable operating points of systems composed of such selfish terminals, and try to come up with a minimum set of rules (etiquette) so as to make sure that the optimality loss compared to a cooperative – centrally controlled setting – is kept at a minimum.M. Felegyhazi and J.P. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Game Theory
Game theory is the study of mathematical models of strategic interactions among rational agents. Myerson, Roger B. (1991). ''Game Theory: Analysis of Conflict,'' Harvard University Press, p.&nbs1 Chapter-preview links, ppvii–xi It has applications in all fields of social science, as well as in logic, systems science and computer science. Originally, it addressed two-person zero-sum games, in which each participant's gains or losses are exactly balanced by those of other participants. In the 21st century, game theory applies to a wide range of behavioral relations; it is now an umbrella term for the science of logical decision making in humans, animals, as well as computers. Modern game theory began with the idea of mixed-strategy equilibria in two-person zero-sum game and its proof by John von Neumann. Von Neumann's original proof used the Brouwer fixed-point theorem on continuous mappings into compact convex sets, which became a standard method in game theory and m ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Cognitive Radio
A cognitive radio (CR) is a radio that can be programmed and configured dynamically to use the best wireless channels in its vicinity to avoid user interference and congestion. Such a radio automatically detects available channels in wireless spectrum, then accordingly changes its transmission or reception parameters to allow more concurrent wireless communications in a given spectrum band at one location. This process is a form of dynamic spectrum management. Description In response to the operator's commands, the cognitive engine is capable of configuring radio-system parameters. These parameters include "waveform, protocol, operating frequency, and networking". This functions as an autonomous unit in the communications environment, exchanging information about the environment with the networks it accesses and other cognitive radios (CRs). A CR "monitors its own performance continuously", in addition to "reading the radio's outputs"; it then uses this information to "determine ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Ekram Hossain
Ekram Hossain is a professor in the Department oElectrical and Computer Engineeringat University of Manitoba, Winnipeg, Manitoba, Canada. Hossain leads the ''Wireless Communications, Networks, and Services Research Group'' at University of Manitoba and is editor-in-chief for the IEEE Communications Surveys and Tutorials. In addition, Hossain has held visiting professorships at the School of Computer Engineering, Nanyang Technological University, Singapore (February 2011, August 2009), Tohoku University, Japan (November 2010), and School of Computer Science and Engineering, The University of New South Wales, Australia Australia, officially the Commonwealth of Australia, is a Sovereign state, sovereign country comprising the mainland of the Australia (continent), Australian continent, the island of Tasmania, and numerous List of islands of Australia, sma ... (June 2008). Hossain's research in wireless communication networks is widely cited. In 2012, he received the Best Pap ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Random Access
Random access (more precisely and more generally called direct access) is the ability to access an arbitrary element of a sequence in equal time or any datum from a population of addressable elements roughly as easily and efficiently as any other, no matter how many elements may be in the set. In computer science it is typically contrasted to sequential access which requires data to be retrieved in the order it was stored. For example, data might be stored notionally in a single sequence like a row, in two dimensions like rows and columns on a surface, or in multiple dimensions. However, given all the coordinates, a program can access each record about as quickly and easily as any other. In this sense, the choice of datum is arbitrary in the sense that no matter which item is sought, all that is needed to find it is its address, i.e. the coordinates at which it is located, such as its row and column (or its track and record number on a magnetic drum). At first, the term "random ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Power Control
Power control, broadly speaking, is the intelligent selection of transmitter power output in a communication system to achieve good performance within the system. Guowang Miao, Jens Zander, Ki Won Sung, and Ben Slimane, Fundamentals of Mobile Data Networks, Cambridge University Press, , 2016. The notion of "good performance" can depend on context and may include optimizing metrics such as link data rate, network capacity, outage probability, geographic coverage and range, and life of the network and network devices. Power control algorithms are used in many contexts, including cellular networks, sensor networks, wireless LANs, and DSL modems. Transmit power control Transmit power control is a technical mechanism used within some networking devices in order to prevent too much unwanted interference between different wireless networks (e.g. the owner's network and the neighbour's network). It is also essential component in case of cognitive radio networks deployed in a distrib ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Quality Of Service
Quality of service (QoS) is the description or measurement of the overall performance of a service, such as a telephony or computer network, or a cloud computing service, particularly the performance seen by the users of the network. To quantitatively measure quality of service, several related aspects of the network service are often considered, such as packet loss, bit rate, throughput, transmission delay, availability, jitter, etc. In the field of computer networking and other packet-switched telecommunication networks, quality of service refers to traffic prioritization and resource reservation control mechanisms rather than the achieved service quality. Quality of service is the ability to provide different priorities to different applications, users, or data flows, or to guarantee a certain level of performance to a data flow. Quality of service is particularly important for the transport of traffic with special requirements. In particular, developers have introduced ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Mesh Networking
A mesh network is a local area network topology in which the infrastructure nodes (i.e. bridges, switches, and other infrastructure devices) connect directly, dynamically and non-hierarchically to as many other nodes as possible and cooperate with one another to efficiently route data to and from clients. This lack of dependency on one node allows for every node to participate in the relay of information. Mesh networks dynamically self-organize and self-configure, which can reduce installation overhead. The ability to self-configure enables dynamic distribution of workloads, particularly in the event a few nodes should fail. This in turn contributes to fault-tolerance and reduced maintenance costs. Mesh topology may be contrasted with conventional star/tree local network topologies in which the bridges/switches are directly linked to only a small subset of other bridges/switches, and the links between these infrastructure neighbours are hierarchical. While star-and-tree topologi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
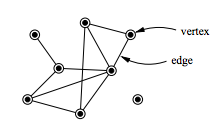
Network Theory
Network theory is the study of graphs as a representation of either symmetric relations or asymmetric relations between discrete objects. In computer science and network science, network theory is a part of graph theory: a network can be defined as a graph in which nodes and/or edges have attributes (e.g. names). Network theory has applications in many disciplines including statistical physics, particle physics, computer science, electrical engineering, biology, archaeology, economics, finance, operations research, climatology, ecology, public health, sociology, and neuroscience. Applications of network theory include logistical networks, the World Wide Web, Internet, gene regulatory networks, metabolic networks, social networks, epistemological networks, etc.; see List of network theory topics for more examples. Euler's solution of the Seven Bridges of Königsberg problem is considered to be the first true proof in the theory of networks. Network optimization Ne ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |