|
Enterprise Mobility Management
Enterprise mobility management (EMM) is the set of people, processes and technology focused on managing mobile devices, wireless networks, and other mobile computing services in a business context. As more workers have bought smartphone and tablet computing devices and have sought support for using these devices in the workplace, EMM has become increasingly significant. The goal of EMM is to determine if and how available mobile IT should be integrated with work processes and objectives, and how to support workers when they are using these devices in the workplace. Business use of consumer mobile technology A 2012 study showed that about two-thirds of smartphone owners used their personal devices for enterprise-related activities. Supporting a wide variety of device types and operating systems can introduce security risks and added costs for businesses. A 2011 survey showed that three quarters of U.K. and U.S. CIOs surveyed considered mobile technology to be a significant sec ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Mobile Device
A mobile device (or handheld computer) is a computer small enough to hold and operate in the hand. Mobile devices typically have a flat LCD or OLED screen, a touchscreen interface, and digital or physical buttons. They may also have a physical keyboard. Many such devices can connect to the Internet and connect with other devices such as car entertainment systems or headsets via Wi-Fi, Bluetooth, cellular networks or near field communication (NFC). Integrated cameras, the ability to place and receive voice and video telephone calls, video games, and Global Positioning System (GPS) capabilities are common. Power is typically provided by a lithium-ion battery. Mobile devices may run mobile operating systems that allow third-party applications to be installed and run. Early smartphones were joined in the late 2000s by larger tablets. Input and output is usually via a touch-screen interface. Phones/tablets and personal digital assistants may provide much of the functionality ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Data Storage
Computer data storage is a technology consisting of computer components and recording media that are used to retain digital data. It is a core function and fundamental component of computers. The central processing unit (CPU) of a computer is what manipulates data by performing computations. In practice, almost all computers use a storage hierarchy, which puts fast but expensive and small storage options close to the CPU and slower but less expensive and larger options further away. Generally, the fast volatile technologies (which lose data when off power) are referred to as "memory", while slower persistent technologies are referred to as "storage". Even the first computer designs, Charles Babbage's Analytical Engine and Percy Ludgate's Analytical Machine, clearly distinguished between processing and memory (Babbage stored numbers as rotations of gears, while Ludgate stored numbers as displacements of rods in shuttles). This distinction was extended in the Von Neuman ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Bring Your Own Device
Bring your own device (BYOD )—also called bring your own technology (BYOT), bring your own phone (BYOP), and bring your own personal computer (BYOPC)—refers to being allowed to use one's personally owned device, rather than being required to use an officially provided device. There are two major contexts in which this term is used. One is in the mobile phone industry, where it refers to carriers allowing customers to activate their existing phone (or other cellular device) on the network, rather than being forced to buy a new device from the carrier. The other, and the main focus of this article, is in the workplace, where it refers to a policy of permitting employees to bring personally owned devices (laptops, tablets, smartphones, etc.) to work, and to use those devices to access privileged company information and applications. This phenomenon is commonly referred to as IT consumerization. BYOD is making significant inroads in the business world, with about 75% of employe ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Mobile Application Management
Mobile application management (MAM) describes the software and services responsible for provisioning and controlling access to internally developed and commercially available mobile apps used in business settings, on both company-provided and 'bring your own' mobile operating systems as used on smartphones and tablet computers. Mobile application management provides granular controls at the application level which enable system administrators to manage and secure application or 'app' data. MAM differs from mobile device management (MDM), which focuses on controlling the entire device, and requires that users enroll or register their device, and install a service agent. While some enterprise mobility management (EMM) suites include a MAM function, their capabilities may be limited in comparison to stand-alone MAM solutions, because EMM suites require a device management profile in order to enable app management capabilities. History Enterprise mobile application management has b ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Mobile Device Management
Mobile device management (MDM) is the administration of mobile devices, such as smartphones, tablet computers, and laptops. MDM is usually implemented with the use of a third-party product that has management features for particular vendors of mobile devices. Though closely related to Enterprise Mobility Management and Unified Endpoint Management, MDM differs slightly from both: unlike MDM, EMM includes mobile information management, BYOD, mobile application management and mobile content management, whereas UEM provides device management for endpoints like desktops, printers, IoT devices, and wearables as well. Overview MDM is typically a deployment of a combination of on-device applications and configurations, corporate policies and certificates, and backend infrastructure, for the purpose of simplifying and enhancing the IT management of end user devices. In modern corporate IT environments, the sheer number and diversity of managed devices (and user behavior) has motivated ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Mobile Security
Mobile security, or mobile device security, is the protection of smartphones, tablets, and laptops from threats associated with wireless computing. It has become increasingly important in mobile computing. The security of personal and business information now stored on smartphones is of particular concern. More and more users and businesses use smartphones not only to communicate, but also to plan and organize both their users' work and private life. Within companies, these technologies are causing profound changes in the organization of information systems and have therefore become the source of new risks. Indeed, smartphones collect and compile an increasing amount of sensitive information to which access must be controlled to protect the privacy of the user and the intellectual property of the company. All smartphones, as computers, are preferred targets of attacks. This is because these devices have family photos, pictures of pets, passwords, and more. For attackers, the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Mobile Business Intelligence
Mobile Business Intelligence (Mobile BI or Mobile Intelligence) is defined as “Mobile BI is a system comprising both technical and organizational elements that present historical and/or real-time information to its users for analysis on mobile devices such as smartphones and tablets (not laptops), to enable effective decision-making and management support, for the overall purpose of increasing firm performance.” (Peters et al., 2016). Business intelligence (BI) refers to computer-based techniques used in spotting, digging-out, and analyzing business data, such as sales revenue by products and/or departments or associated costs and incomes. Although the concept of mobile computing has been prevalent for over a decade, Mobile BI has shown a momentum/growth only very recently. This change has been partly encouraged by a change from the ‘wired world’ to a wireless world with the advantage of smartphones which has led to a new era of mobile computing, especially in the field of BI ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
List Of Mobile Device Management Software ...
This is a list of Mobile Device Management software. General information Discontinued These are the discontinued Mobile Device Management solutions: * Good Technology - acquired by BlackBerry on November 2, 2015. * McAfee EMM - discontinued since January 11, 2017. * Parallels MDM - sales ended on August 31, 2016 but the support is extended up to August 31, 2017. * SAP Afaria MDM - sales ended on August 31, 2016 but the support is extended up to August 31, 2017. * Symantec Mobile Management - End-of-life since October 6, 2014. Partial support extended up to March 1, 2017. References {{reflist Mobile device management Mobile Device Management Mobile device management (MDM) is the administration of mobile devices, such as smartphones, tablet computers, and laptops. MDM is usually implemented with the use of a third-party product that has management features for particular vendors of m ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
OpenSignal
Opensignal is an independent analytics company specialising in "quantifying the mobile-network experience". In August 2014, Opensignal raised a $4 million Series A investment from Qualcomm Ventures, OATV and Passion Capital. Products and services The OpenSignal application points the user in the direction of better phone signal, measures signal strength, data speed and reliability, and displays nearby Wi-Fi networks. Users of the app share information with Opensignal, which is used in their independent maps of carrier coverage and NetworkRank service. As of July 2021 the app has been downloaded over 10 million times. Opensignal NetworkRank is an in-app service comparing the performance of different cellular carriers in particular regions. The service is a part of their carrier maps, which are colour-coded to show areas of strong and weak cell phone signal. The information used is provided by users of the Opensignal application. The company produce regular industry and consum ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Malware
Malware (a portmanteau for ''malicious software'') is any software intentionally designed to cause disruption to a computer, server, client, or computer network, leak private information, gain unauthorized access to information or systems, deprive access to information, or which unknowingly interferes with the user's computer security and privacy. By contrast, software that causes harm due to some deficiency is typically described as a software bug. Malware poses serious problems to individuals and businesses on the Internet. According to Symantec's 2018 Internet Security Threat Report (ISTR), malware variants number has increased to 669,947,865 in 2017, which is twice as many malware variants as in 2016. Cybercrime, which includes malware attacks as well as other crimes committed by computer, was predicted to cost the world economy $6 trillion USD in 2021, and is increasing at a rate of 15% per year. Many types of malware exist, including computer viruses, worms, Trojan horse ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
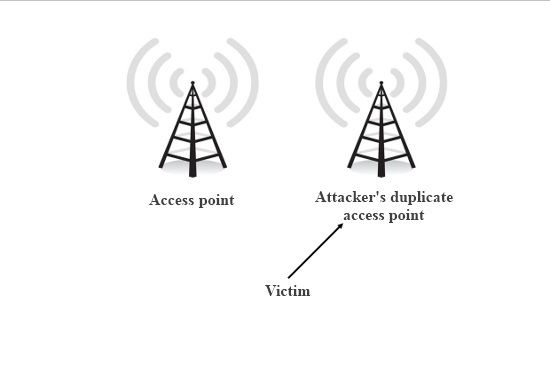
Wireless Network
A wireless network is a computer network that uses wireless data connections between network nodes. Wireless networking is a method by which homes, telecommunications networks and business installations avoid the costly process of introducing cables into a building, or as a connection between various equipment locations. Admin telecommunications networks are generally implemented and administered using radio communication. This implementation takes place at the physical level (layer) of the OSI model network structure. Examples of wireless networks include cell phone networks, wireless local area networks (WLANs), wireless sensor networks, satellite communication networks, and terrestrial microwave networks. History Wireless networks The first professional wireless network was developed under the brand ALOHAnet in 1969 at the University of Hawaii and became operational in June 1971. The first commercial wireless network was the WaveLAN product family, developed by N ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Bring Your Own Device
Bring your own device (BYOD )—also called bring your own technology (BYOT), bring your own phone (BYOP), and bring your own personal computer (BYOPC)—refers to being allowed to use one's personally owned device, rather than being required to use an officially provided device. There are two major contexts in which this term is used. One is in the mobile phone industry, where it refers to carriers allowing customers to activate their existing phone (or other cellular device) on the network, rather than being forced to buy a new device from the carrier. The other, and the main focus of this article, is in the workplace, where it refers to a policy of permitting employees to bring personally owned devices (laptops, tablets, smartphones, etc.) to work, and to use those devices to access privileged company information and applications. This phenomenon is commonly referred to as IT consumerization. BYOD is making significant inroads in the business world, with about 75% of employe ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |