|
End-to-end Auditable Voting Systems
End-to-end auditable or end-to-end voter verifiable (E2E) systems are voting systems with stringent integrity properties and strong tamper resistance. E2E systems often employ cryptographic methods to craft receipts that allow voters to verify that their votes were counted as cast, without revealing which candidates were voted for. As such, these systems are sometimes referred to as receipt-based systems. Overview Electronic voting systems arrive at their final vote totals by a series of steps: # each voter has an original intent, # voters express their intent on ballots (whether interactively, as on the transient display of a DRE voting machine, or durable, as in systems with voter verifiable paper trails), # the ballots are interpreted, to generate electronic cast vote records, # cast vote records are tallied, generating totals # where counting is conducted locally, for example, at the precinct or county level, the results from each local level are combined to produce the fin ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Tamper Resistance
Tamperproofing, conceptually, is a methodology used to hinder, deter or detect unauthorised access to a device or circumvention of a security system. Since any device or system can be foiled by a person with sufficient knowledge, equipment, and time, the term "tamperproof" is a misnomer unless some limitations on the tampering party's resources is explicit or assumed. ''Tamper resistance'' is resistance to tampering (intentional malfunction or sabotage) by either the normal users of a product, package, or system or others with physical access to it. Tamper resistance ranges from simple features like screws with special drives, more complex devices that render themselves inoperable or encrypt all data transmissions between individual chips, or use of materials needing special tools and knowledge. Tamper-resistant devices or features are common on packages to deter package or product tampering. Anti-tamper devices have one or more components: tamper resistance, tamper detectio ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Visual Cryptography
Visual cryptography is a cryptographic technique which allows visual information (pictures, text, etc.) to be encrypted in such a way that the decrypted information appears as a visual image. One of the best-known techniques has been credited to Moni Naor and Adi Shamir, who developed it in 1994. They demonstrated a visual secret sharing scheme, where an image was broken up into ''n'' shares so that only someone with all ''n'' shares could decrypt the image, while any shares revealed no information about the original image. Each share was printed on a separate transparency, and decryption was performed by overlaying the shares. When all ''n'' shares were overlaid, the original image would appear. There are several generalizations of the basic scheme including k-out-of-n visual cryptography, and using opaque sheets but illuminating them by multiple sets of identical illumination patterns under the recording of only one single-pixel detector. Using a similar idea, transparencies can ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Ballot Marking Device
A ballot is a device used to cast votes in an election and may be found as a piece of paper or a small ball used in secret voting. It was originally a small ball (see blackballing) used to record decisions made by voters in Italy around the 16th century. Each voter uses one ballot, and ballots are not shared. In the simplest elections, a ballot may be a simple scrap of paper on which each voter writes in the name of a candidate, but governmental elections use pre-printed ballots to protect the secrecy of the votes. The voter casts their ballot in a box at a polling station. In British English, this is usually called a "ballot paper". The word ''ballot'' is used for an election process within an organization (such as a trade union "holding a ballot" of its members). Etymology The word ballot comes from Italian ''ballotta'', meaning a "small ball used in voting" or a "secret vote taken by ballots" in Venice, Italy. History In ancient Greece, citizens used pieces of broken p ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Invisible Ink
Invisible ink, also known as security ink or sympathetic ink, is a substance used for writing, which is invisible either on application or soon thereafter, and can later be made visible by some means, such as heat or ultraviolet light. Invisible ink is one form of steganography. History One of the earliest writers to mention an invisible ink is Aeneas Tacticus, in the 4th century BC. He mentions it in discussing how to survive under siege but does not indicate the type of ink to be used. This was part of his list of the 20 different methods of secret communications in a book called ''On the Defense of Fortifications''. One of the techniques that involved steganography involved puncturing a tiny hole above or below letters in a document to spell out a secret message. This did not include an invisible ink but the Germans improved on the method during World War I and World War II. They used invisible ink and microdots instead of pinpricks. Philo of Byzantium may be the first write ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
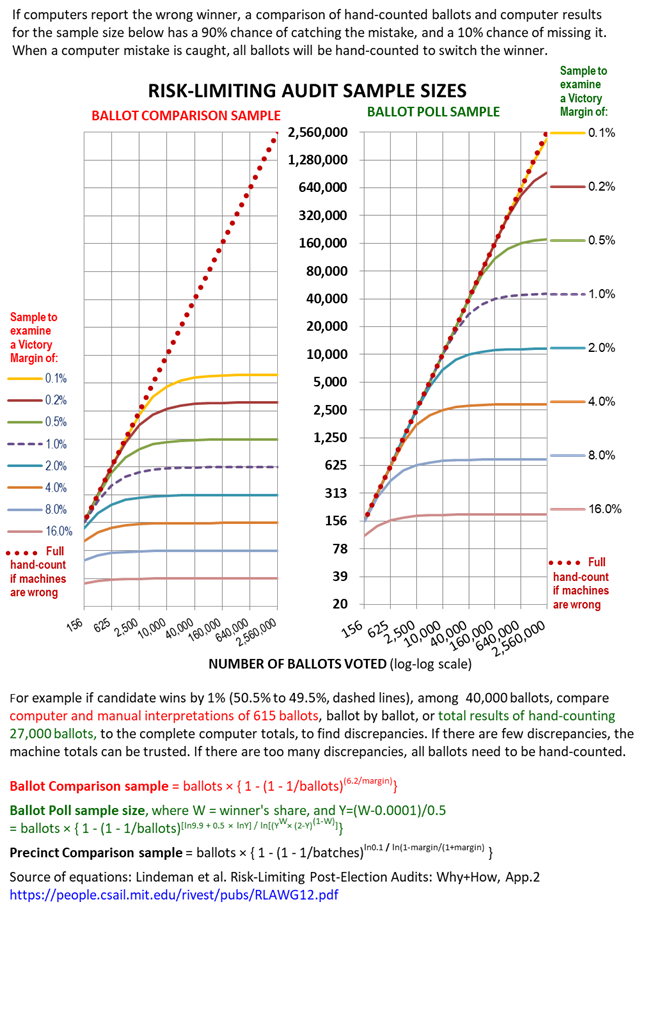
Risk-limiting Audit
A risk-limiting audit (RLA) is a post-election tabulation auditing procedure which can limit the risk that the reported outcome in an election contest is incorrect. It generally involves (1) storing voter-verified paper ballots securely until they can be checked, and (2) manually examining a statistical sample of the paper ballots until enough evidence is gathered to meet the risk limit. Advantages of an RLA include: samples can be small and inexpensive if the margin of victory is large; there are options for the public to watch and verify each step; and errors found in any step lead to corrective actions, including larger samples, up to a 100% hand count if needed. Disadvantages include: the sample needs to be a large fraction of all ballots to minimize the chance of missing mistakes, if any contest is close; and it is hard to check computer totals publicly, except by releasing computer records to the public. If examining sampled ballots shows flaws in ballot storage, the usual a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Scantegrity II
Scantegrity is a security enhancement for optical scan voting systems, providing such systems with end-to-end (E2E) verifiability of election results. It uses confirmation codes to allow a voter to prove to themselves that their ballot is included unmodified in the final tally. The codes are privacy-preserving and offer no proof of which candidate a voter voted for. Receipts can be safely shown without compromising ballot secrecy. ''Scantegrity II'' prints the confirmation codes in invisible ink to improve usability and dispute resolution. As the system relies on cryptographic techniques, the ability to validate an election outcome is both software independent as well as independent of faults in the physical chain-of-custody of the paper ballots. The system was developed by a team of researchers including cryptographers David Chaum and Ron Rivest. Advantages Optical scan voting systems produce an electronic tally, while maintaining the original paper ballots which can be res ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Scantegrity
Scantegrity is a security enhancement for optical scan voting systems, providing such systems with end-to-end (E2E) verifiability of election results. It uses confirmation codes to allow a voter to prove to themselves that their ballot is included unmodified in the final tally. The codes are privacy-preserving and offer no proof of which candidate a voter voted for. Receipts can be safely shown without compromising ballot secrecy. ''Scantegrity II'' prints the confirmation codes in invisible ink to improve usability and dispute resolution. As the system relies on cryptographic techniques, the ability to validate an election outcome is both software independent as well as independent of faults in the physical chain-of-custody of the paper ballots. The system was developed by a team of researchers including cryptographers David Chaum and Ron Rivest. Advantages Optical scan voting systems produce an electronic tally, while maintaining the original paper ballots which can be res ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Ron Rivest
Ronald Linn Rivest (; born May 6, 1947) is a cryptographer and an Institute Professor at MIT. He is a member of MIT's Department of Electrical Engineering and Computer Science (EECS) and a member of MIT's Computer Science and Artificial Intelligence Laboratory (CSAIL). His work has spanned the fields of algorithms and combinatorics, cryptography, machine learning, and election integrity. Rivest is one of the inventors of the RSA algorithm (along with Adi Shamir and Len Adleman). He is the inventor of the symmetric key encryption algorithms RC2, RC4, RC5, and co-inventor of RC6. The "RC" stands for "Rivest Cipher", or alternatively, "Ron's Code". (RC3 was broken at RSA Security during development; similarly, RC1 was never published.) He also authored the MD2, MD4, MD5 and MD6 cryptographic hash functions. Education Rivest earned a Bachelor's degree in Mathematics from Yale University in 1969, and a Ph.D. degree in Computer Science from Stanford University in 19 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
ThreeBallot
ThreeBallot is a voting protocol invented by Ron Rivest in 2006. ThreeBallot is an end-to-end (E2E) auditable voting system that can in principle be implemented on paper. The goal in its design was to provide some of the benefits of a cryptographic voting system without using cryptographic keys. It may be difficult for a vote to be both verifiable and anonymous. ThreeBallot attempts to solve this problem by giving each voter three ballots: one verifiable, and two anonymous. The voter chooses which ballot is verifiable and keeps this secret; since the vote-counter does not know, there is a 1/3 chance of being discovered destroying or altering any single ballot. The voter is forced to make two of their three ballots cancel each other out, so that they can only vote once. Goals The crucial advantages that the ThreeBallot system offers over comparable, ciphered ballots are: # Its implementation is ''familiarly looking and simple for voters to understand'', compared to other en ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Mix Network
Mix networks are routing protocols that create hard-to-trace communications by using a chain of proxy servers known as ''mixes'' which take in messages from multiple senders, shuffle them, and send them back out in random order to the next destination (possibly another mix node). This breaks the link between the source of the request and the destination, making it harder for eavesdroppers to trace end-to-end communications. Furthermore, mixes only know the node that it immediately received the message from, and the immediate destination to send the shuffled messages to, making the network resistant to malicious mix nodes. Each message is encrypted to each proxy using public key cryptography; the resulting encryption is layered like a Russian doll (except that each "doll" is of the same size) with the message as the innermost layer. Each proxy server strips off its own layer of encryption to reveal where to send the message next. If all but one of the proxy servers are comprom ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Prêt à Voter
Prêt à Voter is an E2E voting system devised by Peter Ryan of the University of Luxembourg. It aims to provide guarantees of accuracy of the count and ballot privacy that are independent of software, hardware etc. Assurance of accuracy flows from maximal transparency of the process, consistent with maintaining ballot privacy. In particular, Prêt à Voter enables voters to confirm that their vote is accurately included in the count whilst avoiding dangers of coercion or vote buying. The key idea behind the Prêt à Voter approach is to encode the vote using a randomized candidate list. The randomisation of the candidate list on each ballot form ensures the secrecy of each vote. Incidentally, it also removes any bias towards the top candidate that can occur with a fixed ordering. The value printed on the bottom of the receipt is the key to extraction of the vote. Buried cryptographically in this value is the information needed to reconstruct the candidate order and so extract ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
IEEE Spectrum
''IEEE Spectrum'' is a magazine edited by the Institute of Electrical and Electronics Engineers. The first issue of ''IEEE Spectrum'' was published in January 1964 as a successor to ''Electrical Engineering''. The magazine contains peer-reviewed articles about technology and science trends affecting business and society. In 2010, ''IEEE Spectrum'' was the recipient of ''Utne Reader'' magazine's Utne Independent Press Award for Science/Technology Coverage. In 2012, ''IEEE Spectrum'' was selected as the winner of the National Magazine Awards' "General Excellence Among Thought Leader Magazines" category. References External links * {{Official website, https://spectrum.ieee.org/ Monthly magazines published in the United States Science and technology magazines published in the United States Engineering magazines Spectrum A spectrum (plural ''spectra'' or ''spectrums'') is a condition that is not limited to a specific set of values but can vary, without gaps, across a c ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |