|
Exim Bank Of China
Exim is a mail transfer agent (MTA) used on Unix-like operating systems. Exim is a free software distributed under the terms of the GNU General Public License, and it aims to be a general and flexible mailer with extensive facilities for checking incoming e-mail. Exim has been ported to most Unix-like systems, as well as to Microsoft Windows using the Cygwin emulation layer. Exim 4 is currently the default MTA on Debian Linux systems. Many Exim installations exist, especially within Internet service providers and universities in the United Kingdom. Exim is also widely used with the GNU Mailman mailing list manager, and cPanel. In March 2023 a study performed by E-Soft, Inc., approximated that 59% of the publicly reachable mail-servers on the Internet ran Exim. Origin The first version of Exim was written in 1995 by Philip Hazel for use in the University of Cambridge Computing Service’s e-mail systems. The name initially stood for EXperimental Internet Mailer. It was ori ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Philip Hazel
Philip Hazel is a computer programmer best known for writing the Exim mail transport agent in 1995 and the PCRE regular expression library in 1997. He did undergraduate studies at the University of Cape Town and went to the University of Cambridge for his PhD. He arrived in Cambridge in 1967 where he was employed by the University of Cambridge Computing Service until he retired at the end of September 2007. In 2009 Hazel wrote an autobiographical memoir about his computing career which he updated in 2017. Hazel is also known for his typesetting software, in particular " Philip's Music Writer", as well as programs to turn a simple markup into a subset of DocBook XML for use in the Exim manual, and to produce PostScript PostScript (PS) is a page description language and dynamically typed, stack-based programming language. It is most commonly used in the electronic publishing and desktop publishing realm, but as a Turing complete programming language, it c ... from th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
CPanel
cPanel is web hosting control panel software developed by cPanel, L.L.C. It provides a graphical interface (GUI) and automation tools designed to simplify the process of hosting a web site for the website owner or "end user". It enables administration through a standard web browser using a three-tier structure. While cPanel is limited to managing a single hosting account, cPanel & WHM allow the administration of the entire server. In addition to the GUI, cPanel also has command line and API-based access that allows third-party software vendors, web hosting organizations, and developers to automate standard system administration processes. cPanel & WHM is designed to function either as a dedicated server or virtual private server. The latest cPanel & WHM version supports installation on AlmaLinux, Rocky Linux, CloudLinux OS, and Ubuntu. History cPanel is currently developed by cPanel, L.L.C., a privately owned company headquartered in Houston, Texas, United States. WebPr ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
SMTP
The Simple Mail Transfer Protocol (SMTP) is an Internet standard communication protocol for electronic mail transmission. Mail servers and other message transfer agents use SMTP to send and receive mail messages. User-level email clients typically use SMTP only for sending messages to a mail server for relaying, and typically submit outgoing email to the mail server on port 465 or 587 per . For retrieving messages, IMAP (which replaced the older POP3) is standard, but proprietary servers also often implement proprietary protocols, e.g., Exchange ActiveSync. SMTP's origins began in 1980, building on concepts implemented on the ARPANET since 1971. It has been updated, modified and extended multiple times. The protocol version in common use today has extensible structure with various extensions for authentication, encryption, binary data transfer, and internationalized email addresses. SMTP servers commonly use the Transmission Control Protocol on port number 25 (between ser ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Anti-spam
Various anti-spam techniques are used to prevent email spam (unsolicited bulk email). No technique is a complete solution to the spam problem, and each has trade-offs between incorrectly rejecting legitimate email ( false positives) as opposed to not rejecting all spam email ( false negatives) – and the associated costs in time, effort, and cost of wrongfully obstructing good mail. Anti-spam techniques can be broken into four broad categories: those that require actions by individuals, those that can be automated by email administrators, those that can be automated by email senders and those employed by researchers and law enforcement officials. End-user techniques There are a number of techniques that individuals can use to restrict the availability of their email addresses, with the goal of reducing their chance of receiving spam. Discretion Sharing an email address only among a limited group of correspondents is one way to limit the chance that the address will be "harv ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Anti-virus
Antivirus software (abbreviated to AV software), also known as anti-malware, is a computer program used to prevent, detect, and remove malware. Antivirus software was originally developed to detect and remove computer viruses, hence the name. However, with the proliferation of other malware, antivirus software started to protect against other computer threats. Some products also include protection from malicious URLs, spam, and phishing. History 1971–1980 period (pre-antivirus days) The first known computer virus appeared in 1971 and was dubbed the " Creeper virus". This computer virus infected Digital Equipment Corporation's ( DEC) PDP-10 mainframe computers running the TENEX operating system.From the first email to the first YouTube video: a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Access Control List
In computer security, an access-control list (ACL) is a list of permissions associated with a system resource (object or facility). An ACL specifies which users or system processes are granted access to resources, as well as what operations are allowed on given resources. Each entry in a typical ACL specifies a subject and an operation. For instance, * If a file object has an ACL that contains, this would give Alice permission to read and write the file and give Bob permission only to read it. * If the Resource Access Control Facility (RACF) profile CONSOLE CLASS(TSOAUTH) has an ACL that contains, this would give ALICE permission to use the TSO CONSOLE command. Implementations Many kinds of operating systems implement ACLs or have a historical implementation; the first implementation of ACLs was in the filesystem of Multics in 1965. Filesystem ACLs A filesystem ACL is a data structure (usually a table) containing entries that specify individual user or group rights to ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Backward Compatibility
In telecommunications and computing, backward compatibility (or backwards compatibility) is a property of an operating system, software, real-world product, or technology that allows for interoperability with an older legacy system, or with Input/output, input designed for such a system. Modifying a system in a way that does not allow backward compatibility is sometimes called "wikt:breaking change, breaking" backward compatibility. Such breaking usually incurs various types of costs, such as Switching barriers, switching cost. A complementary concept is ''forward compatibility''; a design that is forward-compatible usually has a Technology roadmap, roadmap for compatibility with future standards and products. Usage In hardware A simple example of both backward and forward compatibility is the introduction of FM broadcasting, FM radio in stereophonic sound, stereo. FM radio was initially monaural, mono, with only one audio channel represented by one signal (electrical engineerin ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
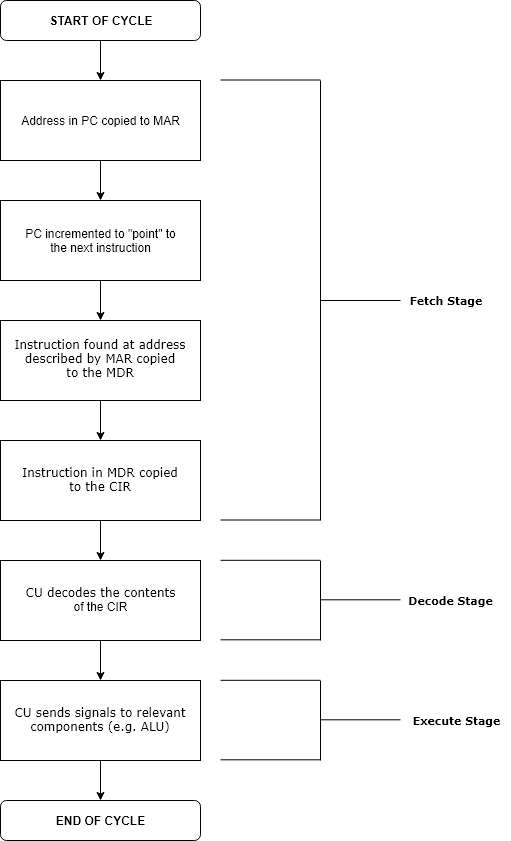
Run Time (program Lifecycle Phase)
Execution in computer and software engineering is the process by which a computer or virtual machine interprets and acts on the instructions of a computer program. Each instruction of a program is a description of a particular action which must be carried out, in order for a specific problem to be solved. Execution involves repeatedly following a " fetch–decode–execute" cycle for each instruction done by the control unit. As the executing machine follows the instructions, specific effects are produced in accordance with the semantics of those instructions. Programs for a computer may be executed in a batch process without human interaction or a user may type commands in an interactive session of an interpreter. In this case, the "commands" are simply program instructions, whose execution is chained together. The term run is used almost synonymously. A related meaning of both "to run" and "to execute" refers to the specific action of a user starting (or ''launching'' o ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Vulnerability (computing)
Vulnerabilities are flaws or weaknesses in a system's design, implementation, or management that can be exploited by a malicious actor to compromise its security. Despite a system administrator's best efforts to achieve complete correctness, virtually all hardware and software contain bugs where the system does not behave as expected. If the bug could enable an attacker to compromise the confidentiality, integrity, or availability of system resources, it can be considered a vulnerability. Insecure software development practices as well as design factors such as complexity can increase the burden of vulnerabilities. Vulnerability management is a process that includes identifying systems and prioritizing which are most important, scanning for vulnerabilities, and taking action to secure the system. Vulnerability management typically is a combination of remediation, mitigation, and acceptance. Vulnerabilities can be scored for severity according to the Common Vulnerability S ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Privilege (computing)
In computing, privilege is defined as the delegation of authority to perform security-relevant functions on a computer system. A privilege allows a user to perform an action with security consequences. Examples of various privileges include the ability to create a new user, install software, or change kernel functions. Users who have been delegated extra levels of control are called privileged. Users who lack most privileges are defined as unprivileged, regular, or normal users. Theory Privileges can either be automatic, granted, or applied for. An automatic privilege exists when there is no requirement to have permission to perform an action. For example, on systems where people are required to log into a system to use it, logging out will not require a privilege. Systems that do not implement file protection - such as MS-DOS - essentially give unlimited privilege to perform any action on a file. A granted privilege exists as a result of presenting some credential to the ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Executable
In computer science, executable code, an executable file, or an executable program, sometimes simply referred to as an executable or binary, causes a computer "to perform indicated tasks according to encoded instruction (computer science), instructions", as opposed to a data (computing), data file that must be interpreted (parser, parsed) by an interpreter (computing), interpreter to be functional. The exact interpretation depends upon the use. "Instructions" is traditionally taken to mean machine code instructions for a physical central processing unit, CPU. In some contexts, a file containing scripting instructions (such as bytecode) may also be considered executable. Generation of executable files Executable files can be hand-coded in machine language, although it is far more convenient to develop software as source code in a high-level language that can be easily understood by humans. In some cases, source code might be specified in assembly language instead, which rema ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Software Design
Software design is the process of conceptualizing how a software system will work before it is implemented or modified. Software design also refers to the direct result of the design process the concepts of how the software will work which consists of both design documentation and undocumented concepts. Software design usually is directed by goals for the resulting system and involves problem-solving and planning including both high-level software architecture and low-level component and algorithm design. In terms of the waterfall development process, software design is the activity of following requirements specification and before coding. General process The design process enables a designer to model various aspects of a software system before it exists. Creativity, past experience, a sense of what makes "good" software, and a commitment to quality are success factors for a competent design. However, the design process is not always a straightforward procedure ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |