|
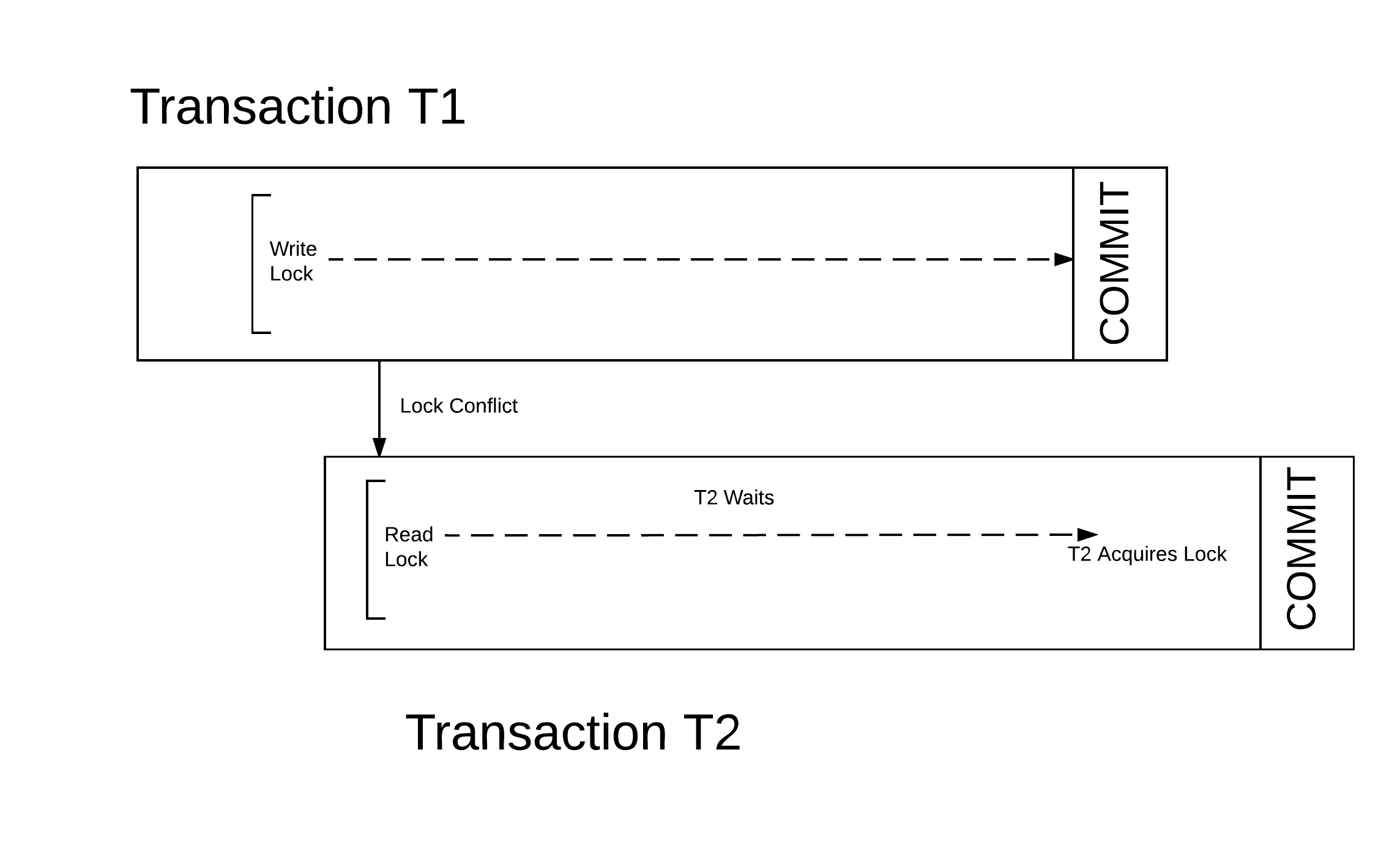
Transactional Memory
In computer science and computer engineering, engineering, transactional memory attempts to simplify concurrent programming by allowing a group of load and store instructions to execute in an linearizability, atomic way. It is a concurrency control mechanism analogous to database transactions for controlling access to Shared memory (interprocess communication), shared memory in concurrent computing. Transactional memory systems provide high-level abstraction as an alternative to low-level thread synchronization. This abstraction allows for coordination between concurrent reads and writes of shared data in parallel systems. Motivation In concurrent programming, synchronization is required when parallel threads attempt to access a shared resource. Low-level thread synchronization constructs such as locks are pessimistic and prohibit threads that are outside a critical section from running the code protected by the critical section. The process of applying and releasing locks often ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Computer Science
Computer science is the study of computation, information, and automation. Computer science spans Theoretical computer science, theoretical disciplines (such as algorithms, theory of computation, and information theory) to Applied science, applied disciplines (including the design and implementation of Computer architecture, hardware and Software engineering, software). Algorithms and data structures are central to computer science. The theory of computation concerns abstract models of computation and general classes of computational problem, problems that can be solved using them. The fields of cryptography and computer security involve studying the means for secure communication and preventing security vulnerabilities. Computer graphics (computer science), Computer graphics and computational geometry address the generation of images. Programming language theory considers different ways to describe computational processes, and database theory concerns the management of re ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Resource Starvation
In computer science, resource starvation is a problem encountered in concurrent computing where a process is perpetually denied necessary resources ''Resource'' refers to all the materials available in our environment which are Technology, technologically accessible, Economics, economically feasible and Culture, culturally Sustainability, sustainable and help us to satisfy our needs and want ... to process its work. Starvation may be caused by errors in a scheduling or mutual exclusion algorithm, but can also be caused by resource leaks, and can be intentionally caused via a denial-of-service attack such as a fork bomb. When starvation is impossible in a concurrent algorithm, the algorithm is called starvation-free, lockout-freed or said to have finite bypass. This property is an instance of liveness, and is one of the two requirements for any mutual exclusion algorithm; the other being correctness. The name "finite bypass" means that any process (concurrent part) of th ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Speculative Multithreading
Thread Level Speculation (TLS), also known as Speculative Multi-threading, or Speculative Parallelization, is a technique to speculatively execute a section of computer code that is anticipated to be executed later in parallel with the normal execution on a separate independent thread. Such a speculative thread may need to make assumptions about the values of input variables. If these prove to be invalid, then the portions of the speculative thread that rely on these input variables will need to be discarded and squashed. If the assumptions are correct the program can complete in a shorter time provided the thread was able to be scheduled efficiently. Description TLS extracts threads from serial code and executes them speculatively in parallel with a safe thread. The speculative thread will need to be discarded or re-run if its presumptions on the input state prove to be invalid. It is a dynamic (runtime) parallelization Parallel computing is a type of computation i ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Transmeta Efficeon
The Efficeon (stylized as efficēon) processor is Transmeta's second-generation 256-bit VLIW design released in 2004 which employs a software engine Code Morphing Software (CMS) to convert code written for x86 processors to the native instruction set of the chip. Like its predecessor, the Transmeta Crusoe (a 128-bit VLIW architecture), Efficeon stresses computational efficiency, low power consumption, and a low thermal footprint. Processor Efficeon most closely mirrors the feature set of Intel Pentium 4 processors, although, like AMD Opteron processors, it supports a fully integrated memory controller, a HyperTransport IO bus, and the NX bit, or no-execute x86 extension to PAE mode. The Efficeon has a 128 KB L1 instruction cache, a 64 KB L1 data cache and a 1 MB L2 cache. All caches are on die. Additionally, the Efficeon CMS (code morphing software) reserves a small portion of main memory (typically 32 MB) for its translation cache of dynamically translated x86 instructions ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Transmeta Crusoe
The Transmeta Crusoe is a family of x86-compatible microprocessors developed by Transmeta and introduced in 2000. Instead of the instruction set architecture being implemented in hardware, or translated by specialized hardware, the Crusoe runs a software abstraction layer, or a virtual machine, known as the Code Morphing Software (CMS). The CMS translates machine code instructions received from programs into native instructions for the microprocessor. In this way, the Crusoe can software emulation, emulate other instruction set architectures (ISAs). This is used to allow the microprocessors to emulate the Intel x86 instruction set. Design The Crusoe is notable for its method of achieving x86 compatibility. Instead of the instruction set architecture being implemented in hardware, or translated by specialized hardware, the Crusoe runs a software abstraction layer, or a virtual machine, known as the Code Morphing Software (CMS). The CMS translates machine code instruction ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Transmeta
Transmeta Corporation was an American fabless semiconductor company based in Santa Clara, California. It developed low power x86 compatible microprocessors based on a VLIW core and a software layer called Code Morphing Software. Code Morphing Software (CMS) consisted of an interpreter, a runtime system and a dynamic binary translator. x86 instructions were first interpreted one instruction at a time and profiled, then depending upon the frequency of execution of a code block, CMS would progressively generate more optimized translations. The VLIW core implemented features specifically designed to accelerate CMS and translations. Among the features were support for general speculation, detection of memory aliasing and detection of self modifying x86 code. The combination of CMS and the VLIW core allowed for the achievement of full x86 compatibility while maintaining performance and reducing power consumption. Transmeta was founded in 1995 by Bob Cmelik, Dave Ditzel, Colin Hu ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Hardware Acceleration
Hardware acceleration is the use of computer hardware designed to perform specific functions more efficiently when compared to software running on a general-purpose central processing unit (CPU). Any transformation of data that can be calculated in software running on a generic CPU can also be calculated in custom-made hardware, or in some mix of both. To perform computing tasks more efficiently, generally one can invest time and money in improving the software, improving the hardware, or both. There are various approaches with advantages and disadvantages in terms of decreased latency, increased throughput, and reduced energy consumption. Typical advantages of focusing on software may include greater versatility, more rapid development, lower non-recurring engineering costs, heightened portability, and ease of updating features or patching bugs, at the cost of overhead to compute general operations. Advantages of focusing on hardware may include speedup, reduced power c ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Compare And Swap
In computer science, compare-and-swap (CAS) is an atomic instruction used in multithreading to achieve synchronization. It compares the contents of a memory location with a given (the previous) value and, only if they are the same, modifies the contents of that memory location to a new given value. This is done as a single atomic operation. The atomicity guarantees that the new value is calculated based on up-to-date information; if the value had been updated by another thread in the meantime, the write would fail. The result of the operation must indicate whether it performed the substitution; this can be done either with a simple boolean response (this variant is often called compare-and-set), or by returning the value read from the memory location (''not'' the value written to it), thus "swapping" the read and written values. Overview A compare-and-swap operation is an atomic version of the following pseudocode, where denotes access through a pointer: function cas(p: poin ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Runtime Library
A runtime library is a library that provides access to the runtime environment that is available to a computer program tailored to the host platform. A runtime environment implements the execution model as required for a development environment such as a particular programming language. A runtime library may provide basic program facilities such as for memory management and exception handling. A runtime library is an artifact of the design of the toolchain used to build the program not inherently required by the host operating system or the programming language in which the program is written. The toolset is designed to abstract aspects of the host platform often to simplify tool development. The toolchain builds a program to depend on a runtime library and to use it while the program is running at program run-time. The runtime library may directly implement runtime behavior, but often it is a thin wrapper on top of operating system facilities. For example, some langua ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Software Transactional Memory
In computer science, software transactional memory (STM) is a concurrency control mechanism analogous to database transactions for controlling access to shared memory in concurrent computing. It is an alternative to lock-based synchronization. STM is a strategy implemented in software, rather than as a hardware component. A transaction in this context occurs when a piece of code executes a series of reads and writes to shared memory. These reads and writes logically occur at a single instant in time; intermediate states are not visible to other (successful) transactions. The idea of providing hardware support for transactions originated in a 1986 paper by Tom Knight.Tom Knight. An architecture for mostly functional languages.' Proceedings of the 1986 ACM conference on Lisp and functional programming. The idea was popularized by Maurice Herlihy and J. Eliot B. Moss.Maurice Herlihy and J. Eliot B. Moss. ''Transactional memory: architectural support for lock-free data structures.'' ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
RISC
In electronics and computer science, a reduced instruction set computer (RISC) is a computer architecture designed to simplify the individual instructions given to the computer to accomplish tasks. Compared to the instructions given to a complex instruction set computer (CISC), a RISC computer might require more instructions (more code) in order to accomplish a task because the individual instructions perform simpler operations. The goal is to offset the need to process more instructions by increasing the speed of each instruction, in particular by implementing an instruction pipeline, which may be simpler to achieve given simpler instructions. The key operational concept of the RISC computer is that each instruction performs only one function (e.g. copy a value from memory to a register). The RISC computer usually has many (16 or 32) high-speed, general-purpose registers with a load–store architecture in which the code for the register-register instructions (for performing ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Load-link/store-conditional
In computer science, load-linked/store-conditional (LL/SC), sometimes known as load-reserved/store-conditional (LR/SC), are a pair of instructions used in multithreading to achieve synchronization. Load-link returns the current value of a memory location, while a subsequent store-conditional to the same memory location will store a new value only if no updates have occurred to that location since the load-link. Together, this implements a lock-free, atomic, read-modify-write operation. "Load-linked" is also known as load-link, load-reserved, and load-locked. LL/SC was originally proposed by Jensen, Hagensen, and Broughton for the S-1 AAP multiprocessor at Lawrence Livermore National Laboratory. Comparison of LL/SC and compare-and-swap If any updates have occurred, the store-conditional is guaranteed to fail, even if the value read by the load-link has since been restored. As such, an LL/SC pair is stronger than a read followed by a compare-and-swap (CAS), which will not de ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |