|
Public Key Infrastructure
A public key infrastructure (PKI) is a set of roles, policies, hardware, software and procedures needed to create, manage, distribute, use, store and revoke digital certificates and manage public-key encryption. The purpose of a PKI is to facilitate the secure electronic transfer of information for a range of network activities such as e-commerce, internet banking and confidential email. It is required for activities where simple passwords are an inadequate authentication method and more rigorous proof is required to confirm the identity of the parties involved in the communication and to validate the information being transferred. In cryptography, a PKI is an arrangement that ''binds'' public keys with respective identities of entities (like people and organizations). The binding is established through a process of registration and issuance of certificates at and by a certificate authority (CA). Depending on the assurance level of the binding, this may be carried out by an ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
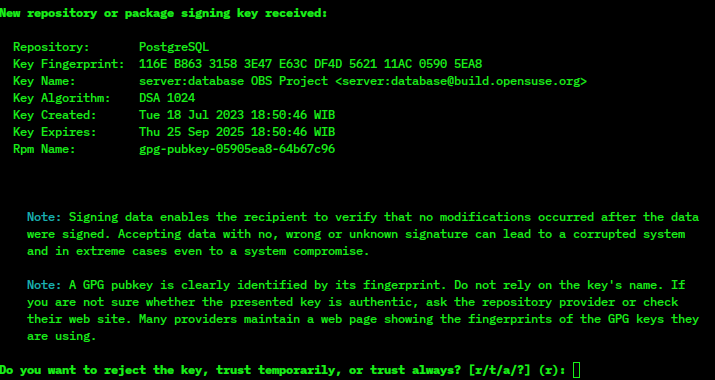
GnuPG
GNU Privacy Guard (GnuPG or GPG) is a free-software replacement for Symantec's cryptographic software suite PGP. The software is compliant with the now obsoleted , the IETF standards-track specification of OpenPGP. Modern versions of PGP are interoperable with GnuPG and other OpenPGP v4-compliant systems. November 2023 saw two drafts aiming to update the 2007 OpenPGP v4 specification (RFC4880), ultimately resulting in thRFC 9580standard in July 2024. The proposal from the GnuPG developers, which is called LibrePGP, was not taken up by the OpenPGP Working Group and future versions of GnuPG will not support the current version of OpenPGP. GnuPG is part of the GNU Project and received major funding from the German government in 1999. Overview GnuPG is a hybrid-encryption software program because it uses a combination of conventional symmetric-key cryptography for speed, and public-key cryptography for ease of secure key exchange, typically by using the recipient's publi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Pretty Good Privacy
Pretty Good Privacy (PGP) is an encryption software, encryption program that provides cryptographic privacy and authentication for data communication. PGP is used for digital signature, signing, encrypting, and decrypting texts, Email, e-mails, files, directories, and whole disk partitions and to increase the security of e-mail communications. Phil Zimmermann developed PGP in 1991. PGP and similar software follow the OpenPGP standard (RFC 4880), an open standard for encryption, encrypting and decrypting data. Modern versions of PGP are interoperability, interoperable with GnuPG and other OpenPGP-compliant systems. The OpenPGP standard has received criticism for its long-lived keys and the difficulty in learning it, as well as the EFAIL, Efail security vulnerability that previously arose when select e-mail programs used OpenPGP with S/MIME. The new OpenPGP standard (RFC 9580) has also been criticised by the maintainer of GnuPG Werner Koch, who in response created his own speci ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
VeriSign
Verisign, Inc. is an American company based in Reston, Virginia, that operates a diverse array of network infrastructure, including two of the Internet's thirteen root nameservers, the authoritative registry for the , , and generic top-level domains and the country-code top-level domains, and the back-end systems for the and sponsored top-level domains. In 2010, Verisign sold its authentication business unit – which included Secure Sockets Layer (SSL) certificate, public key infrastructure (PKI), Verisign Trust Seal, and Verisign Identity Protection (VIP) services – to NortonLifeLock, Symantec for $1.28 billion. The deal capped a multi-year effort by Verisign to narrow its focus to its core infrastructure and security business units. Symantec later sold this unit to DigiCert in 2017. On October 25, 2018, Neustar, NeuStar, Inc. acquired VeriSign's Security Service Customer Contracts. The acquisition effectively transferred Verisign Inc.'s Denial-of-service attack, Distrib ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
GoDaddy
GoDaddy Inc. is an American publicly traded Internet Domain name registry, domain registry, Domain name registrar, domain registrar and web hosting company headquartered in Tempe, Arizona, and incorporated in Delaware. GoDaddy is the world's fifth largest web host by market share, with over 62 million registered domains. The company primarily serves small and micro companies, which make up most of its 20 million customers. History GoDaddy was founded in 1997 in Phoenix, Arizona, by entrepreneur Bob Parsons. Prior to founding GoDaddy, Parsons had sold his financial software services company Parsons Technology to Intuit for $65 million in 1994. He came out of his retirement in 1997 to launch Jomax Technologies, taking its name from a road in Phoenix Arizona. In 1999, a group of employees at Jomax Technologies were brainstorming a new company name, with "Big Daddy" being a popular suggestion. However, finding this domain name already taken, "Go Daddy" was purchased instead. Parson ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Sectigo
Sectigo is a certificate authority and cybersecurity company headquartered in Scottsdale, Arizona. It provides digital certificates, certificate lifecycle management, and public key infrastructure A public key infrastructure (PKI) is a set of roles, policies, hardware, software and procedures needed to create, manage, distribute, use, store and revoke digital certificates and manage public-key encryption. The purpose of a PKI is to fac ... (PKI) services. Standards participation Sectigo participates in the CA/Browser Forum, a voluntary consortium that defines baseline requirements for publicly trusted certificates. Company representatives have contributed to discussions on shorter certificate validity periods and certificate automation practices. References External links * Certificate authorities Computer security companies Companies based in Scottsdale, Arizona Companies with year of establishment missing {{US-company-stub ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
NortonLifeLock
Gen Digital Inc. (formerly Symantec Corporation and NortonLifeLock Inc.) is a multinational software company co-headquartered in both Prague, Czech Republic (European Union, EU) and Tempe, Arizona (United States, USA). The company provides computer security, cybersecurity software and services. Gen is a Fortune 500 company and a member of the S&P 500 stock-market index. It is listed at both Nasdaq, NASDAQ and Prague Stock Exchange. Its portfolio includes Norton (software), Norton, Avast (software), Avast, LifeLock, Avira (software), Avira, AVG (software), AVG, ReputationDefender, MoneyLion and CCleaner. On October 9, 2014, Symantec declared it would split into two independent publicly traded companies by the end of 2015. One company would focus on security, the other on information management. On January 29, 2016, Symantec sold its information-management subsidiary, named Veritas Technologies, Veritas, and which Symantec had acquired in 2004, to The Carlyle Group. On August 8, 2 ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Online Certificate Status Protocol
The Online Certificate Status Protocol (OCSP) is an Internet Communication protocol, protocol used for obtaining the revocation status of an X.509 digital certificate. It was created as an alternative to certificate revocation lists (CRL), specifically addressing certain problems associated with using CRLs in a public key infrastructure (PKI). Messages communicated via OCSP are encoded in ASN.1 and are usually communicated over HTTP. The "request/response" nature of these messages leads to OCSP Server (computing), servers being termed ''OCSP responders''. Some web browsers (e.g., Firefox) use OCSP to validate HTTPS certificates, while others have disabled it. Most OCSP revocation statuses on the Internet disappear soon after certificate expiration. Certificate authority, Certificate authorities (CAs) were previously required by the CA/Browser Forum to provide OCSP service, but this requirement was removed in July 2023 , making OCSP optional and CRLs required again. Let's Encrypt ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
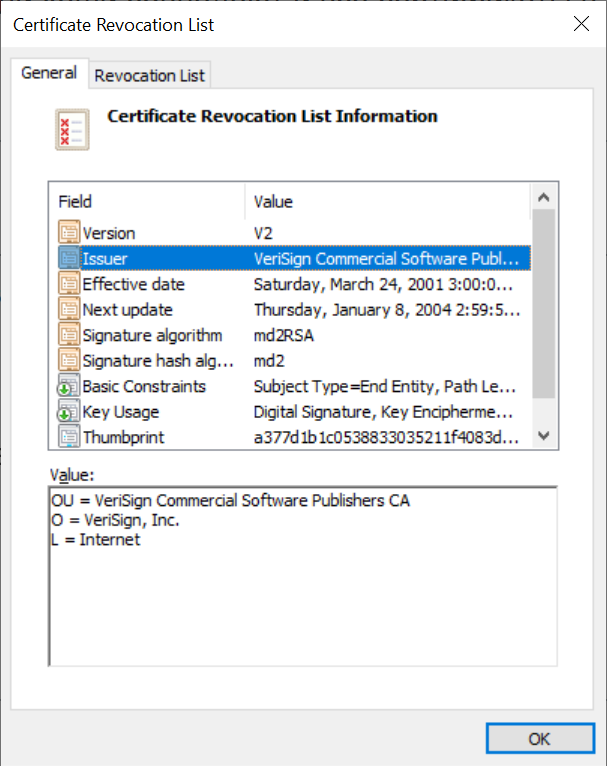
Certificate Revocation Lists
In cryptography, a certificate revocation list (CRL) is "a list of digital certificates that have been revoked by the issuing certificate authority (CA) before their scheduled expiration date and should no longer be trusted". Publicly trusted CAs in the Web PKI are required (including by the CA/Browser forum) to issue CRLs for their certificates, and they widely do. Browsers and other relying parties might use CRLs, or might use alternate certificate revocation technologies (such as OCSP) or CRLSets (a dataset derived from CRLs) to check certificate revocation status. Note that OCSP is falling out of favor due to privacy and performance concerns. Subscribers and other parties can also use ARI. Revocation states There are two different states of revocation defined in RFC 5280: ; Revoked: A certificate is irreversibly revoked if, for example, it is discovered that the certificate authority (CA) had improperly issued a certificate, or if a private-key is thought to have been c ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Web Browsers
A web browser, often shortened to browser, is an application for accessing websites. When a user requests a web page from a particular website, the browser retrieves its files from a web server and then displays the page on the user's screen. Browsers can also display content stored locally on the user's device. Browsers are used on a range of devices, including desktops, laptops, tablets, smartphones, smartwatches and consoles. As of 2024, the most used browsers worldwide are Google Chrome (~66% market share), Safari (~16%), Edge (~6%), Firefox (~3%), Samsung Internet (~2%), and Opera (~2%). As of 2023, an estimated 5.4 billion people had used a browser. Function The purpose of a web browser is to fetch content and display it on the user's device. This process begins when the user inputs a Uniform Resource Locator (URL), such as ''https://en.wikipedia.org/'', into the browser's address bar. Virtually all URLs on the Web start with either ''http:'' or ''https:'' whi ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |