|
Computer Appliance
A computer appliance is a computer system with a combination of Computer hardware, hardware, software, or firmware that is specifically designed to provide a particular computing resource. Such devices became known as ''appliances'' because of the similarity in role or management to a home appliance, which are generally ''closed and sealed'', and are not serviceable by the user or owner. The hardware and software are delivered as an integrated product and may even be pre-configured before delivery to a customer, to provide a turn-key solution for a particular application. Unlike general purpose computers, appliances are generally not designed to allow the customers to change the software and the underlying operating system, or to flexibly reconfigure the hardware. Another form of appliance is the virtual appliance, which has similar functionality to a dedicated hardware appliance, but is distributed as a software virtual machine image for a hypervisor-equipped device. Overview ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
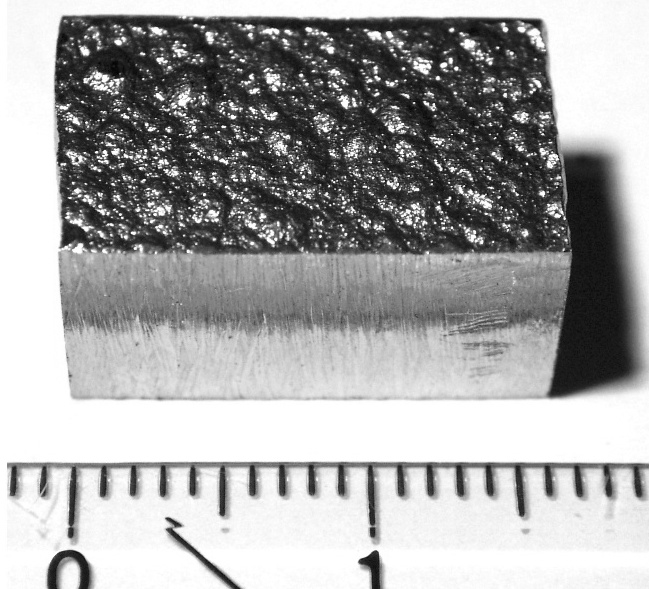
Cobalt Qube 3 Front
Cobalt is a chemical element; it has Symbol (chemistry), symbol Co and atomic number 27. As with nickel, cobalt is found in the Earth's crust only in a chemically combined form, save for small deposits found in alloys of natural meteoric iron. The free element, produced by reductive smelting, is a hard, lustrous, somewhat brittle, gray metal. Cobalt-based blue pigments (cobalt blue) have been used since antiquity for jewelry and paints, and to impart a distinctive blue tint to glass. The color was long thought to be due to the metal bismuth. Miners had long used the name ''kobold ore'' (German language, German for ''goblin ore'') for some of the blue pigment-producing minerals. They were so named because they were poor in known metals and gave off poisonous arsenic-containing fumes when smelted. In 1735, such ores were found to be reducible to a new metal (the first discovered since ancient times), which was ultimately named for the ''kobold''. Today, some cobalt is produced sp ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Disk Mirroring
In Data storage device, data storage, disk mirroring is the Replication (computing), replication of logical disk volumes onto separate physical hard disks in Real-time computing, real time to ensure continuous availability. It is most commonly used in RAID 1. A mirrored volume is a complete logical representation of separate volume copies. In a IT disaster recovery, disaster recovery context, mirroring data over long distance is referred to as storage replication. Depending on the technologies used, replication can be performed synchronously, Asynchronous communication, asynchronously, semi-synchronously, or point-in-time. Replication is enabled via microcode on the disk array controller or via Server (computing), server software. It is typically a proprietary solution, not compatible between various data storage device vendors. Mirroring is typically only synchronous. Synchronous writing typically achieves a recovery point objective (RPO) of zero lost data. Asynchronous replica ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
ODBC
In computing, Open Database Connectivity (ODBC) is a standard application programming interface (API) for accessing database management systems (DBMS). The designers of ODBC aimed to make it independent of database systems and operating systems. An application written using ODBC can be Porting, ported to other platforms, both on the client and server side, with few changes to the data access code. ODBC accomplishes DBMS independence by using an ''ODBC Driver (software), driver'' as a translation layer between the application and the DBMS. The application uses ODBC functions through an ''ODBC driver manager'' with which it is linked, and the driver passes the Query language, query to the DBMS. An ODBC driver can be thought of as analogous to a printer driver or other driver, providing a standard set of functions for the application to use, and implementing DBMS-specific functionality. An application that can use ODBC is referred to as "ODBC-compliant". Any ODBC-compliant application ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Manufacturing Execution System
Manufacturing execution systems (MES) are computerized systems used in manufacturing to track and document the transformation of raw materials to finished goods. MES provides information that helps manufacturing decision-makers understand how current conditions on the plant floor can be optimized to improve production output. MES works as real-time monitoring system to enable the control of multiple elements of the production process (e.g. inputs, personnel, machines and support services). MES may operate across multiple function areas, for example management of product definitions across the product life-cycle, resource scheduling, order execution and dispatch, production analysis and downtime management for overall equipment effectiveness (OEE), product quality, or materials track and trace. MES creates the "as-built" record, capturing the data, processes and outcomes of the manufacturing process. This can be especially important in regulated industries, such as food and bev ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Automation Protocol
This is a list of communication protocols used for the automation of processes (industrial or otherwise), such as for building automation, power-system automation, automatic meter reading, and vehicular automation. Process automation protocols * AS-i – Actuator-sensor interface, a low level 2-wire bus establishing power and communications to basic digital and analog devices * BSAP – Bristol Standard Asynchronous Protocol, developed by Bristol Babcock Inc. * CC-Link Industrial Networks – Supported by the CLPA * CIP (Common Industrial Protocol) – can be treated as application layer common to DeviceNet, CompoNet, ControlNet and EtherNet/IP *ControlNet – an implementation of CIP, originally by Allen-Bradley *DeviceNet – an implementation of CIP, originally by Allen-Bradley * DF-1 - used by Allen-Bradley ControlLogix, CompactLogix, PLC-5, SLC-500, and MicroLogix class devices * DNP3 - a protocol used to communicate by industrial control and utility SCADA systems * Direc ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Security Appliance
A security appliance is any form of server appliance that is designed to protect computer networks from unwanted traffic. Types of security appliances * Active devices block unwanted traffic. Examples of such devices are firewalls, anti virus scanning devices, and content filtering devices. * Passive devices detect and report on unwanted traffic, such as intrusion detection appliances. * Preventative devices scan networks and identify potential security problems (such as penetration testing A penetration test, colloquially known as a pentest, is an authorized simulated cyberattack on a computer system, performed to evaluate the security of the system; this is not to be confused with a vulnerability assessment. The test is performed ... and vulnerability assessment appliances). * Unified Threat Management (UTM) appliances combine features together into one system, such as some firewalls, content filtering, web caching etc. References Server appliance {{compu-networ ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Backup And Disaster Recovery Appliance
In information technology, a backup, or data backup is a copy of computer data taken and stored elsewhere so that it may be used to restore the original after a data loss event. The verb form, referring to the process of doing so, is "back up", whereas the noun and adjective form is "backup". Backups can be used to recover data after its loss from data deletion or corruption, or to recover data from an earlier time. Backups provide a simple form of IT disaster recovery; however not all backup systems are able to reconstitute a computer system or other complex configuration such as a computer cluster, active directory server, or database server. A backup system contains at least one copy of all data considered worth saving. The data storage requirements can be large. An information repository model may be used to provide structure to this storage. There are different types of data storage devices used for copying backups of data that is already in secondary storage onto archive ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Multiplexing
In telecommunications and computer networking, multiplexing (sometimes contracted to muxing) is a method by which multiple analog or digital signals are combined into one signal over a shared medium. The aim is to share a scarce resource—a physical transmission medium. For example, in telecommunications, several telephone calls may be carried using one wire. Multiplexing originated in telegraphy in the 1870s, and is now widely applied in communications. In telephony, George Owen Squier is credited with the development of telephone carrier multiplexing in 1910. The multiplexed signal is transmitted over a communication channel such as a cable. The multiplexing divides the capacity of the communication channel into several logical channels, one for each message signal or data stream to be transferred. A reverse process, known as demultiplexing, extracts the original channels on the receiver end. A device that performs the multiplexing is called a multiplexer (MUX), and a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
EbXML
Electronic Business using eXtensible Markup Language, commonly known as e-business XML, or ebXML (pronounced ee-bee-ex-em-el, 'bi,eks,em'el as it is typically referred to, is a family of XML based standards sponsored by OASIS and UN/CEFACT whose mission is to provide an open, XML-based infrastructure that enables the global use of electronic business information in an interoperable, secure, and consistent manner by all trading partners. The ebXML architecture is a unique set of concepts; part theoretical and part implemented in the existing ebXML standards work. The ebXML work stemmed from earlier work on ooEDI (object oriented EDI), UML / UMM, XML markup technologies and the X12 EDI "Future Vision" work sponsored by ANSI X12 EDI. The melding of these components began in the original ebXML work and the theoretical discussion continues today. Other work relates, such as the Object Management Group work and the OASIS BCM (Business-Centric Methodology) standard (2006). Conce ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Message Oriented Middleware
Message-oriented middleware (MOM) is software or hardware infrastructure supporting sending and receiving messages between distributed systems. Message-oriented middleware is in contrast to streaming-oriented middleware where data is communicated as a sequence of bytes with no explicit message boundaries. Note that streaming protocols are almost always built above protocols using discrete messages such as frames (Ethernet), datagrams ( UDP), packets ( IP), cells ( ATM), et al. MOM allows application modules to be distributed over heterogeneous platforms and reduces the complexity of developing applications that span multiple operating systems and network protocols. The middleware creates a distributed communications layer that insulates the application developer from the details of the various operating systems and network interfaces. Application programming interfaces (APIs) that extend across diverse platforms and networks are typically provided by MOM. This middleware layer ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Transport Layer Security
Transport Layer Security (TLS) is a cryptographic protocol designed to provide communications security over a computer network, such as the Internet. The protocol is widely used in applications such as email, instant messaging, and voice over IP, but its use in securing HTTPS remains the most publicly visible. The TLS protocol aims primarily to provide security, including privacy (confidentiality), integrity, and authenticity through the use of cryptography, such as the use of certificates, between two or more communicating computer applications. It runs in the presentation layer and is itself composed of two layers: the TLS record and the TLS handshake protocols. The closely related Datagram Transport Layer Security (DTLS) is a communications protocol that provides security to datagram-based applications. In technical writing, references to "(D)TLS" are often seen when it applies to both versions. TLS is a proposed Internet Engineering Task Force (IETF) standard, fir ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Firewall (computing)
In computing, a firewall is a network security system that monitors and controls incoming and outgoing network traffic based on configurable security rules. A firewall typically establishes a barrier between a trusted network and an untrusted network, such as the Internet or between several VLANs. Firewalls can be categorized as network-based or host-based. History The term '' firewall'' originally referred to a wall to confine a fire within a line of adjacent buildings. Later uses refer to similar structures, such as the metal sheet separating the engine compartment of a vehicle or aircraft from the passenger compartment. The term was applied in the 1980s to network technology that emerged when the Internet was fairly new in terms of its global use and connectivity. The predecessors to firewalls for network security were routers used in the 1980s. Because they already segregated networks, routers could filter packets crossing them. Before it was used in real-life comput ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |