|
Common Criteria
The Common Criteria for Information Technology Security Evaluation (referred to as Common Criteria or CC) is an international standard (International Organization for Standardization, ISO/International Electrotechnical Commission, IEC 15408) for computer security certification. It is currently in version 3.1 revision 5. Common Criteria is a framework in which computer system users can ''specify'' their security ''functional'' and ''assurance'' requirements (SFRs and SARs, respectively) in a Security Target (ST), and may be taken from Protection Profiles (PPs). Vendors can then ''implement'' or make claims about the security attributes of their products, and testing laboratories can ''evaluate'' the products to determine if they actually meet the claims. In other words, Common Criteria provides assurance that the process of specification, implementation and evaluation of a computer security product has been conducted in a rigorous and standard and repeatable manner at a level that is ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
International Standard
An international standard is a technical standard developed by one or more international standards organizations. International standards are available for consideration and use worldwide. The most prominent such organization is the International Organization for Standardization (ISO). Other prominent international standards organizations including the International Telecommunication Union (ITU) and the International Electrotechnical Commission (IEC). Together, these three organizations have formed the World Standards Cooperation alliance. Purpose International standards can be applied directly or adapted to meet local conditions. When adopted, they lead to the creation of national standards that are either equivalent to or largely align with the international standards in technical content, though they may have: (i) editorial variations, such as differences in appearance, the use of symbols, measurement units, or the choice of a point over a comma as the decimal marker, and (ii) va ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
IT Baseline Protection
The IT baseline protection () approach from the German Federal Office for Information Security (BSI) is a methodology to identify and implement computer security measures in an organization. The aim is the achievement of an adequate and appropriate level of security for IT systems. To reach this goal the BSI recommends "well-proven technical, organizational, personnel, and infrastructural safeguards". Organizations and federal agencies show their systematic approach to secure their IT systems (e.g. Information Security Management System) by obtaining an ''ISO/IEC 27001 Certificate on the basis of IT-Grundschutz''. Overview baseline security The term baseline security signifies standard security measures for typical IT systems. It is used in various contexts with somewhat different meanings. For example: * Microsoft Baseline Security Analyzer: Software tool focused on Microsoft operating system and services security Cisco security baseline Vendor recommendation focused on network a ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
ISO 17025
ISO/ IEC 17025 General requirements for the competence of testing and calibration laboratories is the main standard used by testing and calibration laboratories. In most countries, ISO/IEC 17025 is the standard for which most labs must hold accreditation in order to be deemed technically competent. In many cases, suppliers and regulatory authorities will not accept test or calibration results from a lab that is not accredited. Originally known as ISO/IEC Guide 25, ISO/IEC 17025 was initially issued by ISO/IEC in 1999. There are many commonalities with the ISO 9000 standard, but ISO/IEC 17025 is more specific in requirements for competence and applies directly to those organizations that produce testing and calibration results and is based on more technical principles. Laboratories use ISO/IEC 17025 to implement a quality system aimed at improving their ability to consistently produce valid results. Material in the standard also forms the basis for accreditation from an accreditati ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Common Criteria Testing Laboratory
The Common Criteria model provides for the separation of the roles of evaluator and certifier. Product certificates are awarded by national schemes on the basis of evaluations carried by independent testing laboratories. A Common Criteria testing laboratory is a third-party commercial security testing facility that is accredited to conduct security evaluations for conformance to the Common Criteria international standard. Such facility must be accredited according to ISO/IEC 17025 with its national certification body. Examples List of laboratory designations by country: *In the US they are called Common Criteria Testing Laboratory (CCTL) *In Canada they are called Common Criteria Evaluation Facility (CCEF) *In the UK they are called Commercial Evaluation Facilities (CLEF) *In France they are called Centres d’Evaluation de la Sécurité des Technologies de l’Information (CESTI) *In Germany they are called IT Security Evaluation Facility (ITSEF) Common Criteria Recognition Arra ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
National Institute Of Standards And Technology
The National Institute of Standards and Technology (NIST) is an agency of the United States Department of Commerce whose mission is to promote American innovation and industrial competitiveness. NIST's activities are organized into Outline of physical science, physical science laboratory programs that include Nanotechnology, nanoscale science and technology, engineering, information technology, neutron research, material measurement, and physical measurement. From 1901 to 1988, the agency was named the National Bureau of Standards. History Background The Articles of Confederation, ratified by the colonies in 1781, provided: The United States in Congress assembled shall also have the sole and exclusive right and power of regulating the alloy and value of coin struck by their own authority, or by that of the respective states—fixing the standards of weights and measures throughout the United States. Article 1, section 8, of the Constitution of the United States, ratified i ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
National Security Agency
The National Security Agency (NSA) is an intelligence agency of the United States Department of Defense, under the authority of the director of national intelligence (DNI). The NSA is responsible for global monitoring, collection, and processing of information and data for global intelligence and counterintelligence purposes, specializing in a discipline known as signals intelligence (SIGINT). The NSA is also tasked with the protection of U.S. communications networks and information systems. The NSA relies on a variety of measures to accomplish its mission, the majority of which are clandestine. The NSA has roughly 32,000 employees. Originating as a unit to decipher coded communications in World War II, it was officially formed as the NSA by President Harry S. Truman in 1952. Between then and the end of the Cold War, it became the largest of the U.S. intelligence organizations in terms of personnel and budget. Still, information available as of 2013 indicates that the C ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Rainbow Series
The Rainbow Series (sometimes known as the Rainbow Books) is a series of computer security standards and guidelines published by the United States government in the 1980s and 1990s. They were originally published by the U.S. Department of Defense Computer Security Center, and then by the National Computer Security Center. Objective These standards describe a process of evaluation for trusted systems. In some cases, U.S. government entities (as well as private firms) would require formal verification and validation, validation of computer technology using this process as part of their procurement criteria. Many of these standards have influenced, and have been superseded by, the Common Criteria. The books have nicknames based on the color of its cover. For example, the TCSEC, Trusted Computer System Evaluation Criteria was referred to as "The Orange Book." In the book entitled ''Applied Cryptography'', security expert Bruce Schneier states of NCSC-TG-021 that he "can't even be ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
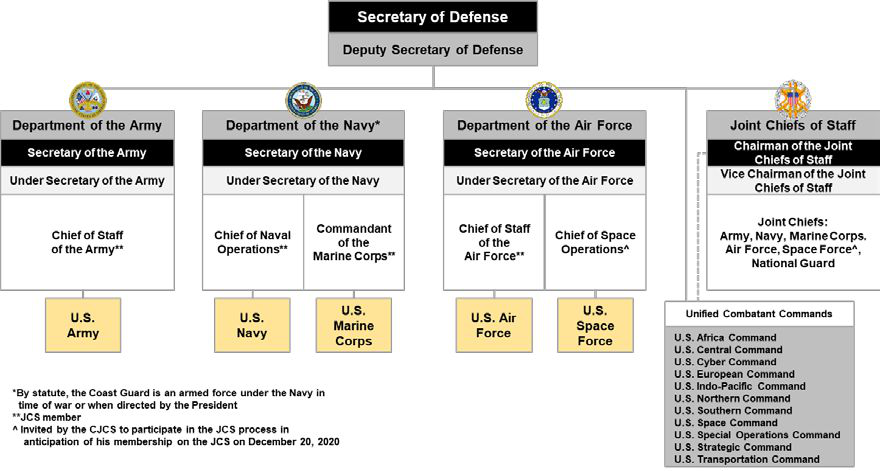
United States Department Of Defense
The United States Department of Defense (DoD, USDOD, or DOD) is an United States federal executive departments, executive department of the federal government of the United States, U.S. federal government charged with coordinating and supervising the six U.S. armed services: the United States Army, Army, United States Navy, Navy, United States Marine Corps, Marines, United States Air Force, Air Force, United States Space Force, Space Force, the United States Coast Guard, Coast Guard for some purposes, and related functions and agencies. As of November 2022, the department has over 1.4 million active-duty uniformed personnel in the six armed services. It also supervises over 778,000 National Guard (United States), National Guard and reservist personnel, and over 747,000 civilians, bringing the total to over 2.91 million employees. Headquartered at the Pentagon in Arlington County, Virginia, just outside Washington, D.C., the Department of Defense's stated mission is "to provid ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
TCSEC
Trusted Computer System Evaluation Criteria (TCSEC) is a United States Government Department of Defense (DoD) standard that sets basic requirements for assessing the effectiveness of computer security controls built into a computer system. The TCSEC was used to evaluate, classify, and select computer systems being considered for the processing, storage, and retrieval of sensitive or classified information. The TCSEC, frequently referred to as the Orange Book, is the centerpiece of the DoD ''Rainbow Series'' publications. Initially issued in 1983 by the National Computer Security Center (NCSC), an arm of the National Security Agency, and then updated in 1985, TCSEC was eventually replaced by the Common Criteria international standard, originally published in 2005. History By the late 1960s, government agencies, like other computer users, had gone far in the transition from batch processing to multiuser and time-sharing systems. The US Department of Defense (DoD) Advanced Resear ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
CTCPEC
The Canadian Trusted Computer Product Evaluation Criteria (CTCPEC) is a computer security standard published in 1993 by the Communications Security Establishment to provide an evaluation criterion on IT products. It is a combination of the TCSEC (also called ''Orange Book'') and the European ITSEC approaches. CTCPEC led to the creation of the Common Criteria standard. The Canadian System Security Centre, part of the Communications Security Establishment The Communications Security Establishment (CSE; , ''CST''), formerly (from 2008-2014) called the Communications Security Establishment Canada (CSEC), is the Government of Canada's national cryptologic agency. It is responsible for foreign signal ... was founded in 1988 to establish a Canadian computer security standard. The Centre published a draft of the standard in April 1992. The final version was published in January 1993. References External links * Computer security standards {{Standard-stub ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
Department Of Trade And Industry (United Kingdom)
The Department of Trade and Industry (DTI) was a United Kingdom government department formed on 19 October 1970. It was replaced with the creation of the Department for Business, Enterprise and Regulatory Reform and the Department for Innovation, Universities and Skills on 28 June 2007. History The department was formed on 19 October 1970 through the merger of the Board of Trade and the Ministry of Technology, creating a new cabinet post of Secretary of State for Trade and Industry. Additionally, the department also took over the Department of Employment's former responsibilities for monopolies and mergers. However, in January 1974, the department's responsibilities for energy production were transferred to a newly created Department of Energy. On 5 March that year, following a Labour Party victory in the February 1974 general election, the department was split into the Department of Trade, the Department of Industry and the Department of Prices and Consumer Protection. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |
GCHQ
Government Communications Headquarters (GCHQ) is an intelligence and security organisation responsible for providing signals intelligence (SIGINT) and information assurance (IA) to the government and armed forces of the United Kingdom. Primarily based at The Doughnut in the suburbs of Cheltenham, GCHQ is the responsibility of the country's Secretary of State for Foreign and Commonwealth Affairs (Foreign Secretary), but it is not a part of the Foreign Office and its director ranks as a Permanent Secretary. GCHQ was originally established after the First World War as the Government Code and Cypher School (GC&CS) and was known under that name until 1946. During the Second World War it was located at Bletchley Park, where it was responsible for breaking the German Enigma codes. There are two main components of GCHQ, the Composite Signals Organisation (CSO), which is responsible for gathering information, and the National Cyber Security Centre (NCSC), which is responsible for ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] |