|
Blue Team (computer Security)
A blue team is a group of individuals who perform an analysis of information systems to ensure security, identify security flaws, verify the effectiveness of each security measure, and make certain all security measures will continue to be effective after implementation. Some blue team objectives include: * Using risk intelligence and digital footprint analysis to find and fix vulnerabilities and prevent possible security incidents. * Conduct regular security audits such as incident response and recovery. History As part of the United States computer security defense initiative, red teams were developed to exploit other malicious entities that would do them harm. As a result, blue teams were developed to design defensive measures against such red team activities. Incident response If an incident does occur within the organization, the blue team will perform the following six steps to handle the situation: #Preparation #Identification #Containment #Eradication #Recovery #Lessons ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
|
 |
Information Systems
An information system (IS) is a formal, sociotechnical, organizational system designed to collect, process, store, and distribute information. From a sociotechnical perspective, information systems comprise four components: task, people, structure (or roles), and technology. Information systems can be defined as an integration of components for collection, storage and processing of data, comprising digital products that process data to facilitate decision making and the data being used to provide information and contribute to knowledge. A computer information system is a system, which consists of people and computers that process or interpret information. The term is also sometimes used to simply refer to a computer system with software installed. "Information systems" is also an academic field of study about systems with a specific reference to information and the complementary networks of computer hardware and software that people and organizations use to collect, filter, p ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
|
Rapid7
The Metasploit Project is a computer security project that provides information about security vulnerabilities and aids in penetration testing and IDS signature development. It is owned by Boston, Massachusetts-based security company, Rapid7. Its best-known sub-project is the open-source Metasploit Framework, a tool for developing and executing exploit code against a remote target machine. Other important sub-projects include the Opcode Database, shellcode archive and related research. The Metasploit Project includes anti-forensic and evasion tools, some of which are built into the Metasploit Framework. In various operating systems it comes pre installed. History Metasploit was created by H. D. Moore in 2003 as a portable network tool using Perl. By 2007, the Metasploit Framework had been completely rewritten in Ruby. On October 21, 2009, the Metasploit Project announced that it had been acquired by Rapid7, a security company that provides unified vulnerability managemen ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
|
|
White Hat (computer Security)
A white hat (or a white-hat hacker, a whitehat) is an ethical security hacker. Ethical hacking is a term meant to imply a broader category than just penetration testing. Under the owner's consent, white-hat hackers aim to identify any vulnerabilities or security issues the current system has. The white hat is contrasted with the black hat, a malicious hacker; this definitional dichotomy comes from Western films, where heroic and antagonistic cowboys might traditionally wear a white and a black hat, respectively. There is a third kind of hacker known as a grey hat who hacks with good intentions but at times without permission. White-hat hackers may also work in teams called " sneakers and/or hacker clubs", red teams, or tiger teams. History One of the first instances of an ethical hack being used was a "security evaluation" conducted by the United States Air Force, in which the Multics operating systems were tested for "potential use as a two-level (secret/top secret) system. ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
|
|
Vulnerability Management
Vulnerability management is the "cyclical practice of identifying, classifying, prioritizing, remediating, and mitigating" software vulnerabilities. Vulnerability management is integral to computer security and network security, and must not be confused with vulnerability assessment. Vulnerabilities can be discovered with a vulnerability scanner, which analyzes a computer system in search of known vulnerabilities,Anna-Maija Juuso and Ari Takanen ''Unknown Vulnerability Management'', Codenomicon whitepaper, October 201 such as open ports, insecure software configurations, and susceptibility to malware infections. They may also be identified by consulting public sources, such as NVD, vendor specific security updates or subscribing to a commercial vulnerability alerting service. Unknown vulnerabilities, such as a zero-day, may be found with fuzz testing. Fuzzing is a cornerstone technique where random or semi-random input data is fed to programs to detect unexpected behavior. T ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
|
|
List Of Digital Forensics Tools
During the 1980s, most digital forensics, digital forensic investigations consisted of "live analysis", examining digital media directly using non-specialist tools. In the 1990s, several freeware and other proprietary tools (both hardware and software) were created to allow investigations to take place without modifying media. This first set of tools mainly focused on computer forensics, although in recent years similar tools have evolved for the field of mobile device forensics. This list includes notable examples of digital forensic tools. Forensics-focused operating systems Debian-based * Kali Linux is a Debian-derived Linux distribution designed for digital forensics and penetration testing, formerly known as BackTrack. * Parrot Security OS is a cloud computing, cloud-oriented Linux distribution based on Debian and designed to perform security and penetration tests, do forensic analysis, or act in anonymity. It uses the MATE Desktop Environment, Linux Kernel 4.6 or higher ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
|
|
Cyber Threat Intelligence
Cyber threat intelligence (CTI) is a subfield of cybersecurity that focuses on the structured collection, analysis, and dissemination of data regarding potential or existing cyber threats. It provides organizations with the insights necessary to anticipate, prevent, and respond to cyberattacks by understanding the behavior of threat actors, their tactics, and the vulnerabilities they exploit. Cyber threat intelligence sources include open source intelligence, social media intelligence, human Intelligence, technical intelligence, device log files, forensically acquired data or intelligence from the internet traffic and data derived for the deep and dark web. In recent years, threat intelligence has become a crucial part of companies' cyber security strategy since it allows companies to be more proactive in their approach and determine which threats represent the greatest risks to a business. This puts companies on a more proactive front, actively trying to find their vulnera ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
|
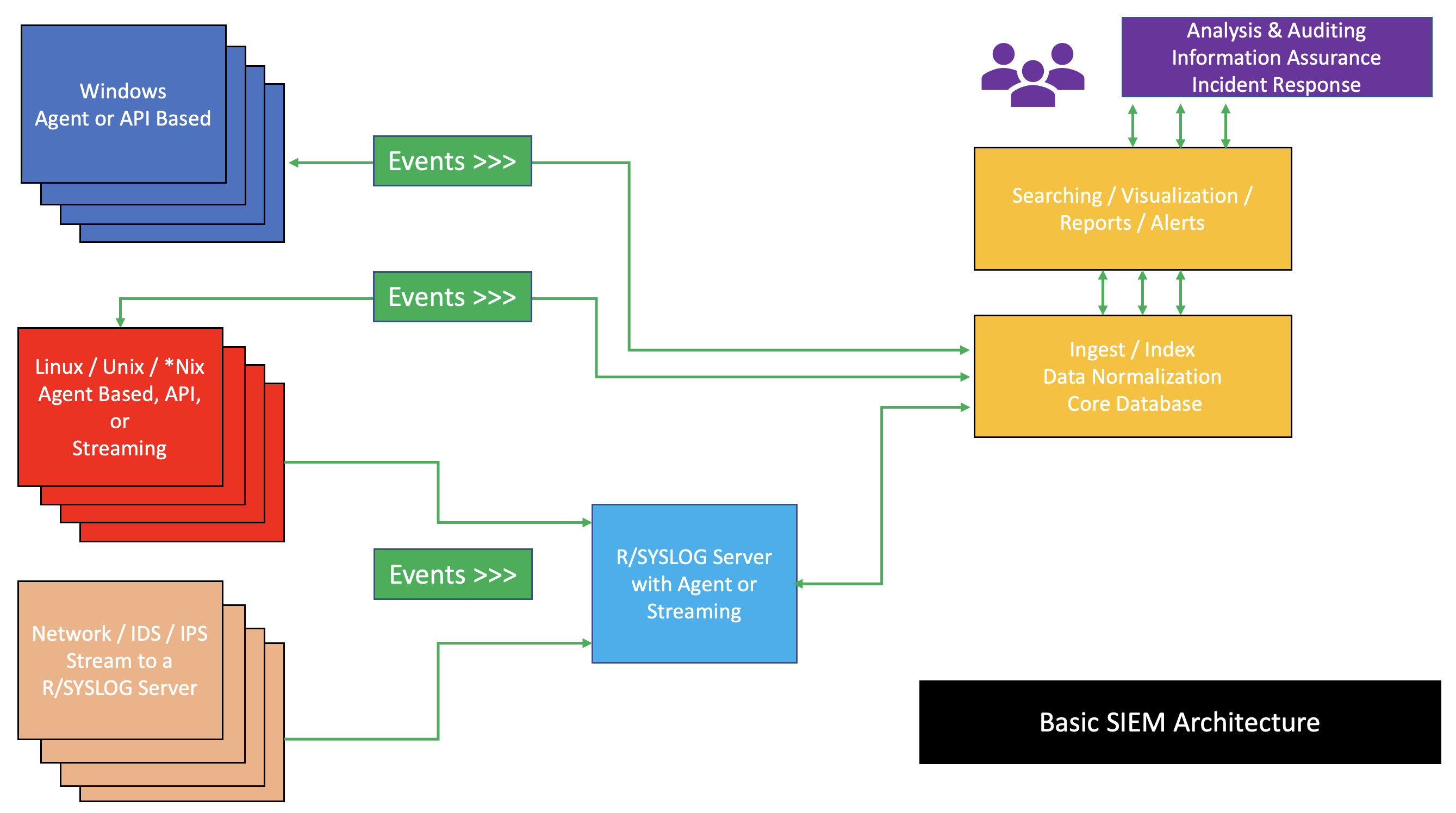 |
Security Information And Event Management
Security information and event management (SIEM) is a field within computer security that combines security information management (SIM) and security event management (SEM) to enable real-time analysis of security alerts generated by applications and network hardware. SIEM systems are central to Security operations center, security operations centers (SOCs), where they are employed to detect, investigate, and respond to security incidents. SIEM technology collects and aggregates data from various systems, allowing organizations to meet compliance requirements while safeguarding against Cyberattack, threats. National Institute of Standards and Technology (NIST) definition for SIEM tool is application that provides the ability to gather security data from information system components and present that data as actionable information via a single interface. SIEM tools can be implemented as software, hardware, or managed services. SIEM systems log security events and generating reports to ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
 |
Splunk
Splunk Inc. is an American software company based in San Francisco, California, that produces software for searching, monitoring, and analyzing machine-generated data via a web-style interface. Its software helps capture, index and correlate real-time data in a searchable Content repository, repository, from which it can generate graphs, reports, alerts, dashboards and visualizations. The firm uses machine data for identifying Pattern recognition, data patterns, providing metrics, diagnosing problems and providing intelligence for business operations. It is a Horizontal market, horizontal technology used for application management, Information security, security and Compliance (regulation), compliance, as well as business and web analytics. In September 2023, it was announced that Splunk would be acquired by Cisco for $28 billion in an all-cash deal. The transaction was completed on March 18, 2024. History Founding & early years Michael Baum (entrepreneur), Michael Baum, R ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
|
SolarWinds
SolarWinds Corporation is an American company that develops software for businesses to help manage their networks, systems, and information technology infrastructure. It is headquartered in Austin, Texas, with sales and product development offices in a number of locations in the United States and several other countries. The company was publicly traded from May 2009 until the end of 2015, and again from October 2018. It has also acquired a number of other companies, some of which it still operates under their original names, including Pingdom, Papertrail, and Loggly. It had about 300,000 customers as of December 2020, including nearly all ''Fortune'' 500 companies and numerous agencies of the US federal government. A SolarWinds product, Orion, used by about 33,000 public and private sector customers, was the focus of a U.S. federal government data leak in 2020. The attack persisted undetected for months in 2020, and additional details about the breadth and depth of compromis ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
|
|
Netwitness
NetWitness is a network security company that provides real-time network forensics automated threat detection, response, and analysis solutions. The company is based in Bedford, Massachusetts. In 2011, NetWitness was acquired by EMC Corporation and in 2020 was acquired by Symphony Technology Group as a stand-alone business unit, part of RSA Security. History In the mid-1990s the NetWitness technology was established by CTX Corporation, a Washington D.C.–based system integrator. The technology, initially chartered as a US Government research project, was created to help analysts better understand large volumes of captured network data for various types of investigations. CTX Corporation was subsequently acquired by ManTech International Corporation () in December 2002. In November 2006, NetWitness Corporation was spun out of Mantech, by Nick Lantuh, who was brought in to run the NetWitness Product Group and execute the spin-out. As an independent company, NetWitness focused ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
|
|
United States
The United States of America (USA), also known as the United States (U.S.) or America, is a country primarily located in North America. It is a federal republic of 50 U.S. state, states and a federal capital district, Washington, D.C. The 48 contiguous states border Canada to the north and Mexico to the south, with the semi-exclave of Alaska in the northwest and the archipelago of Hawaii in the Pacific Ocean. The United States asserts sovereignty over five Territories of the United States, major island territories and United States Minor Outlying Islands, various uninhabited islands in Oceania and the Caribbean. It is a megadiverse country, with the world's List of countries and dependencies by area, third-largest land area and List of countries and dependencies by population, third-largest population, exceeding 340 million. Its three Metropolitan statistical areas by population, largest metropolitan areas are New York metropolitan area, New York, Greater Los Angeles, Los Angel ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |
|
|
Microsoft Azure
Microsoft Azure, or just Azure ( /ˈæʒər, ˈeɪʒər/ ''AZH-ər, AY-zhər'', UK also /ˈæzjʊər, ˈeɪzjʊər/ ''AZ-ure, AY-zure''), is the cloud computing platform developed by Microsoft. It has management, access and development of applications and services to individuals, companies, and governments through its global infrastructure. It also provides capabilities that are usually not included within other cloud platforms, including software as a service (SaaS), platform as a service (PaaS), and infrastructure as a service (IaaS). Microsoft Azure supports many programming languages, tools, and frameworks, including Microsoft-specific and third-party software and systems. Azure was first introduced at the Professional Developers Conference (PDC) in October 2008 under the codename "Project Red Dog". It was officially launched as Windows Azure in February 2010 and later renamed to Microsoft Azure on March 25, 2014. Services Microsoft Azure uses large-scale virtualizati ... [...More Info...] [...Related Items...] OR: [Wikipedia] [Google] [Baidu] [Amazon] |